Watchtower Overview
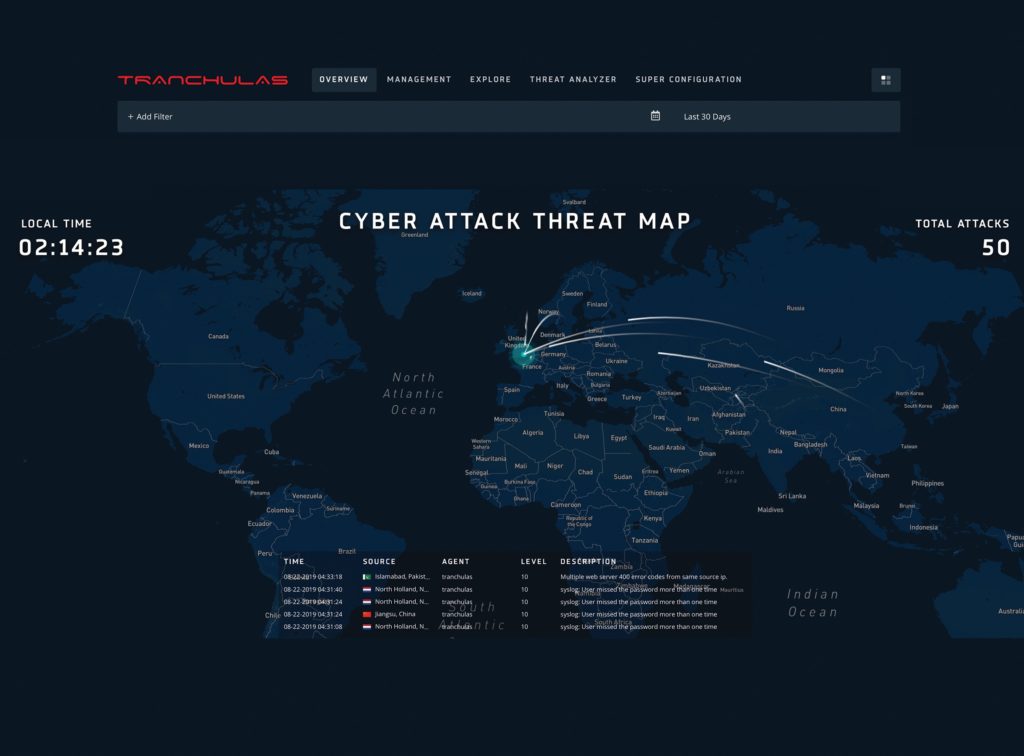
Cyber Threat Map
Tranchulas Cyber Threat Map shows you live cyber-attacks on your organization. Tranchulas Watchtower displays the geographic location of hacker and your systems on the map which are being targeted along with the timestamp, severity of attack and attack details. Security Analysts can visualize attacks and hacker behaviour from around the world.
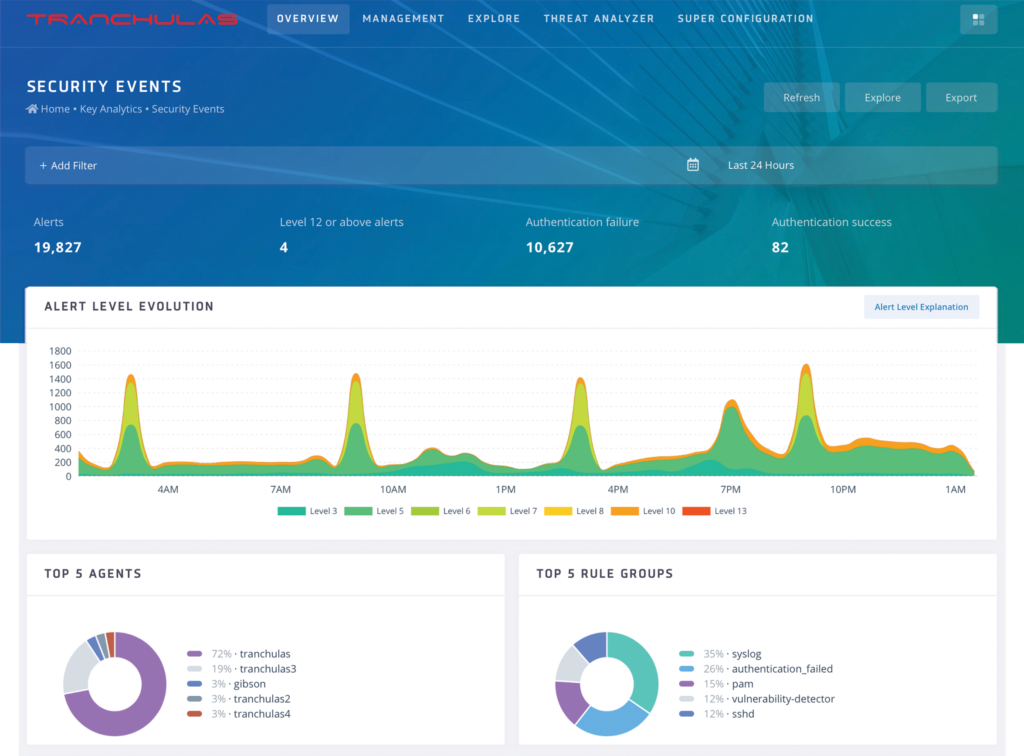
Security Events
Tranchulas Watchtower helps you visualise and analyse security events. You can see security events of any machine in your organisation, search events and filter them using visualisations.
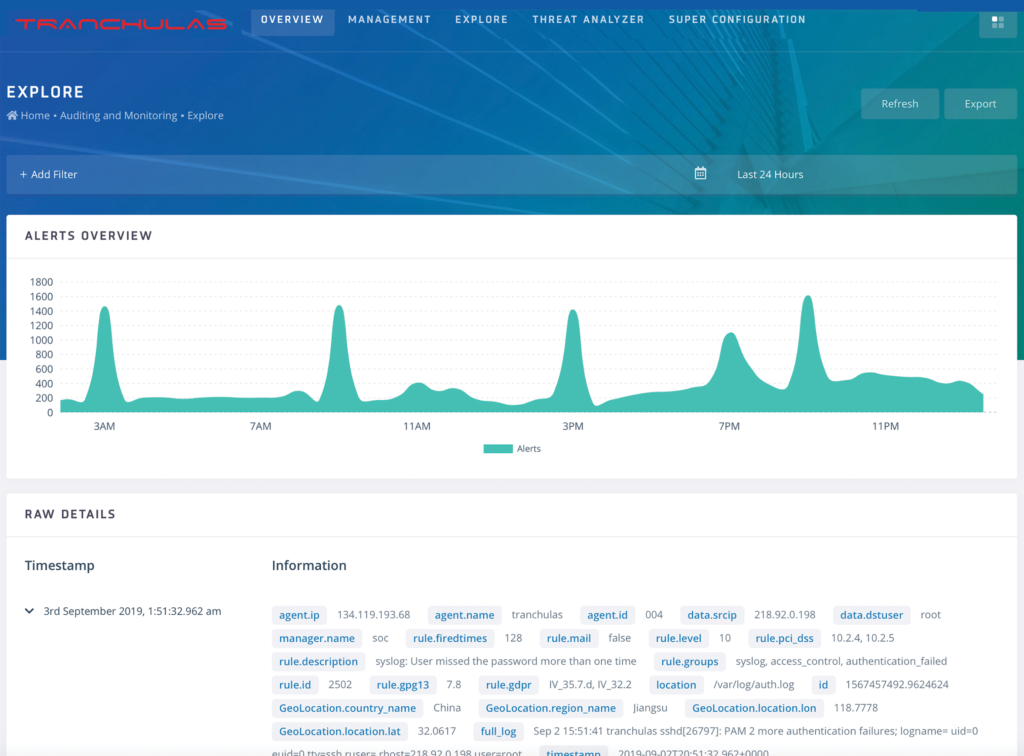
Log Collection
Tranchulas Watchtower collects log data from servers, workstations and network devices including firewalls and IDS/IPS in real-time. Logs can be sent via Tranchulas-SOC agent or remote Syslog. The logs are analyzed by Watchtower to identify intrusion attempts, security vulnerabilities, policy violations and application/system errors.
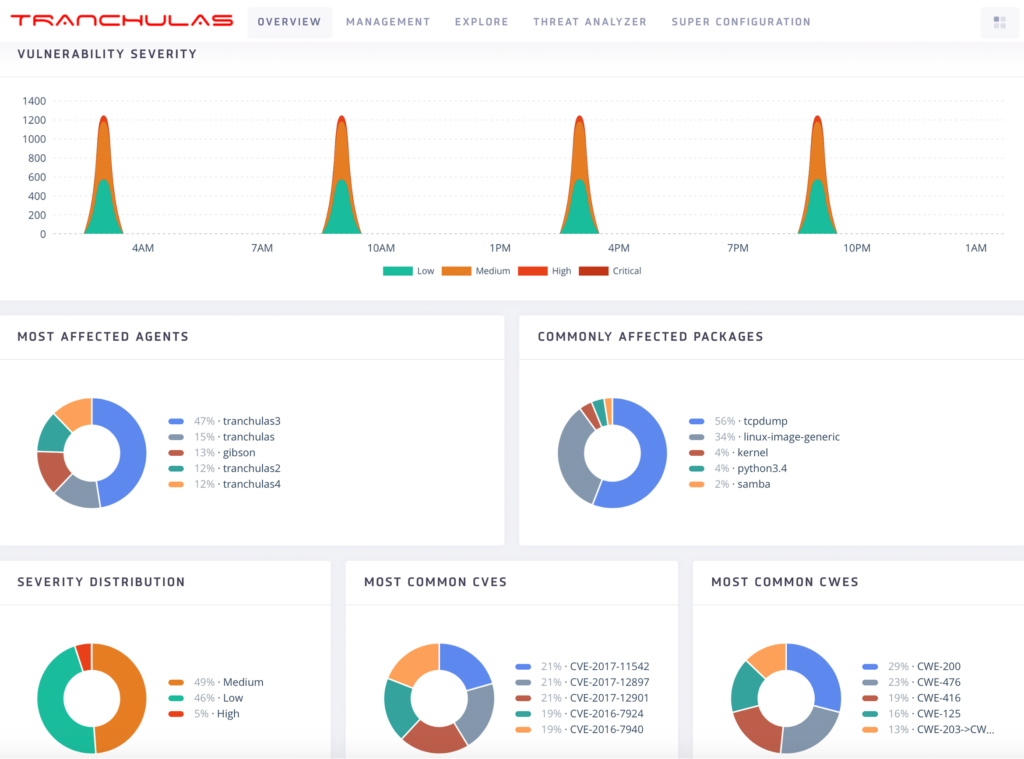
Vulnerability Detection
We periodically run vulnerability scans which help us identify weaknesses in your environment and take corrective actions before malicious hackers exploit them.
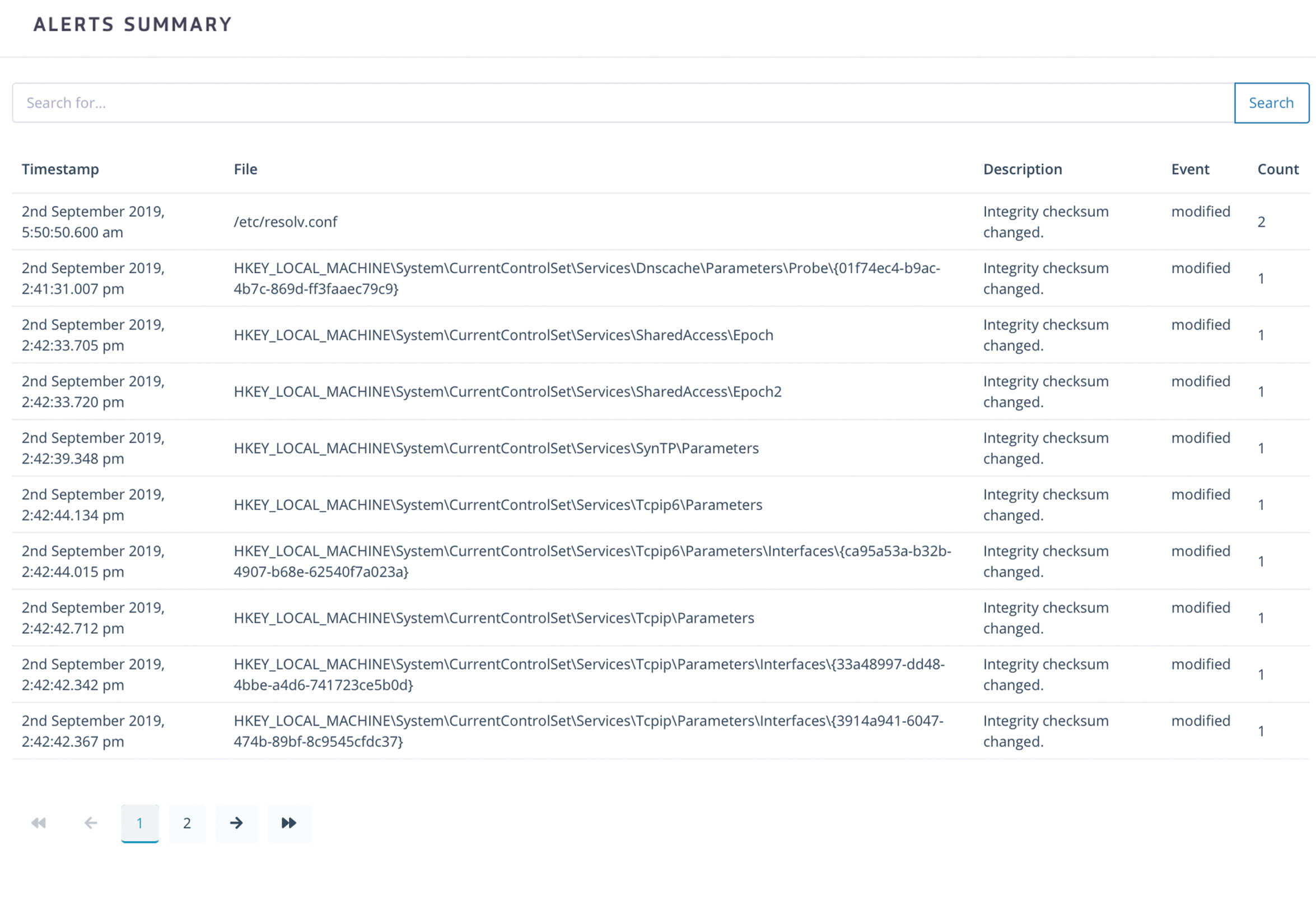
File Integrity Monitoring
Tranchulas Watchtower monitors selected files and folder. An alert is triggered every time the monitored file is modified or a new file is added in the selected folders.
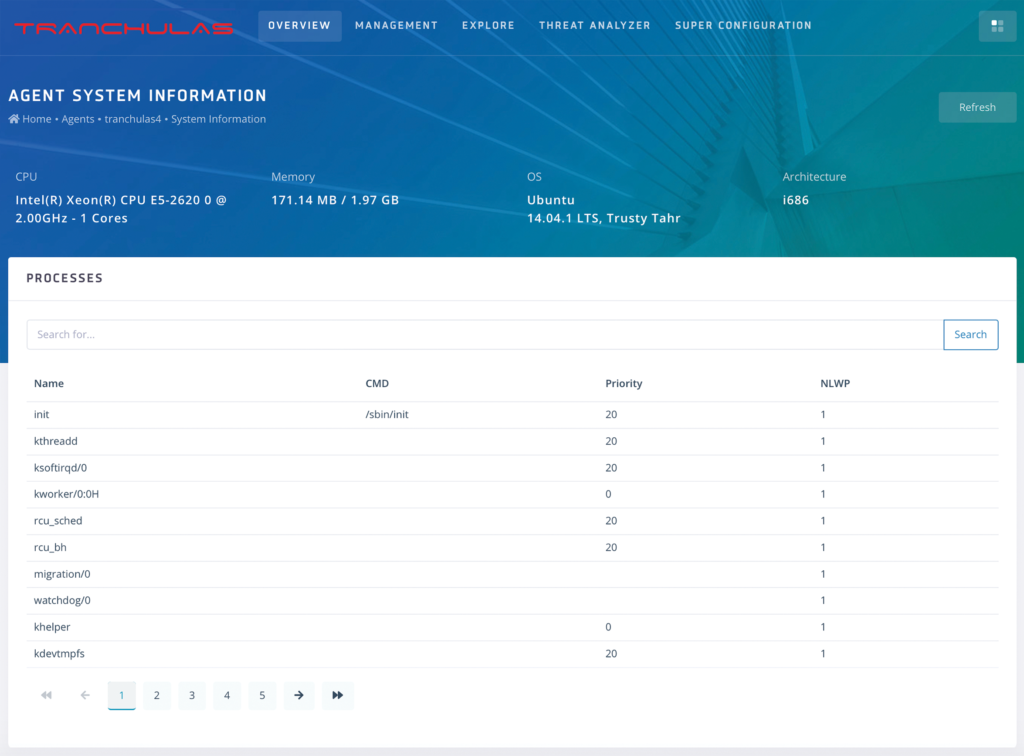
System Inventory
Tranchulas Watchtower is able to maintain the system inventory of servers and workstations in your organization. This includes hardware details, operating system, open ports, installed software and running processes.
Need Help?
Let one of our experts guide you through our SOC platform.
